
Do you want to learn more about phishing so you can improve your understanding and defend your business against phishing attacks? This blog will provide you with the information you need to start learning about this critical topic.
According to the GOV website, ‘The most common threat by far is phishing – staff receiving fraudulent emails or being directed to fraudulent websites.’
What are Phishing attacks?
Phishing can affect businesses of any size and usually comes in the form of an email. Typically, this will consist of a fraudulent message intended to trick the user into handing over sensitive or personal information. The hacker may also attempt to convince the victim to download malicious software. These attacks can have disastrous effects on individuals and businesses who fall victim to this scam.
Phishing has become a significant issue for businesses in recent times. Hackers took advantage of the pandemic, using panic and urgency to lure users into their scams. The move to remote working for many businesses also provided another opportunity for hackers as this BBC article suggests; ‘56% of senior IT technicians believe their employees have picked up bad cyber-security habits while working from home. Worryingly, the survey found that many employees agreed with that assessment.’
A great way to start defending your business against phishing attacks is to improve your knowledge of phishing. You can then go on to start the conversation and share this information with your employees

How to spot Phishing emails
There are different types of phishing attacks, and some are easier to spot than others. An organisation may be part of a mass campaign. This is where an attacker sends a generic scam email to collect data quickly to sell on. Alternatively, it could be a more specific targeted attack. This aims to reveal certain sensitive data about the business or an individual within the company.
A significant first step in learning about phishing emails is familiarising yourself with some common key characteristics and looking at some basic examples.
Tips for spotting scam emails:
- The domain name looks unusual or contains typos. Always check the actual email address, not just the display name.
- There is usually an urgent call to action in the form of a link or attachment.
- The message is badly worded and poorly written. Either in the email address, subject or body of text itself.
- The email contains a generic greeting, a legitimate email will usually address you personally.
- If you receive an email from someone you know but it seems suspicious, send a brand new email. Don’t just hit reply and never click on any attachments or URLs.
- Never input any personal or sensitive data. Most legitimate companies will never ask you to provide things like an address, date of birth, passwords or card information via email. If unsure, email the company directly in a separate thread.
- Check the URLs. In many email clients (such as Microsoft Outlook), you can hover your mouse pointer over any links in an email (without actually clicking on it!). A popup box should appear showing where that link is actually going to take you, which is often somewhere very different to where you might expect.
- If something seems too good to be true, it probably is. Hackers use the promise of something fantastic to lure victims in.
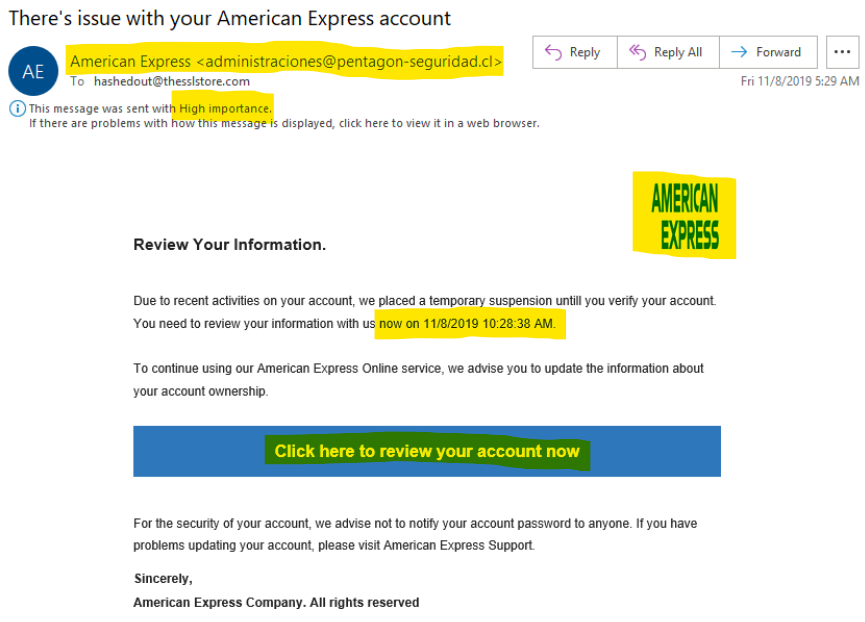
The above image is a classic example of a scam email. Note the display name beside the actual email address, the squished logo and the sense of urgency it is creating.
Although these tips will help identify the obvious scam emails that may come into your inbox, hackers are becoming increasingly good at disguising their scams to look as legitimate as possible. It is always best to contact your IT team if you are ever unsure about a particular email.
What happens to your data
If hackers manage to obtain your valuable data, there are various ways that they may use it. Attackers can use personal information like full names, addresses, and birth dates in identity theft scams. Hackers can also use card details to clone a card and make purchases without the victim’s knowledge. Personal and financial data is often the prime target for hackers as this is quick and easy to sell on. However, hackers also prey on business and healthcare data, usually with the motivation of extortion or as a way to access further information about clients or customers.
For many, the most significant consequence of a business falling victim to a phishing attack is the loss of customer trust and loyalty. Customers rely on organisations to store and protect their sensitive data. Companies should ensure they have correct security measures in place. Reputation is an essential aspect to grow and maintain for any business. Trust and loyalty in your company and brand is one of many reasons why defending your business from phishing attacks is vital to all companies.

What should I do if I come across a potential phishing email?
It’s always better to be safe than sorry. The best way to tackle phishing scams is to prevent them. If you are suspicious of any emails you receive, never call any numbers provided within the message or click on any attachments or links within the email. Do not input any personal or sensitive information and inform your IT team as soon as possible.
Although many phishing emails can be easy to spot, some may appear legitimate. If you do happen to click on a link or feel that your information is compromised, your next steps depend on the type of scam you have encountered. Contact authorities and your bank first if you think the hackers will have access to any sensitive personal information or financial details. If you have access to an IT expert, let them know as soon as possible and ask if they can look into the issue for you.
There is also a helpful link on the National Cyber Security Centre website that allows you to report any suspicious emails or websites that you come across. When a report is received, they will then analyse and monitor the email or website and act on the report if necessary.
How to prevent phishing attacks
Although the tips above are a great start, the best way to protect against phishing attacks is to educate yourself or your employees on the subject. Be aware of the issue, practice common sense, exercise caution and never trust threatening emails.
Wytech can provide specific phishing training, as well as conduct simulated phishing attacks. Simulated attacks provide us with information on how robust your systems are and highlight any area that may need attention regarding your cyber security.
Share this article with your family, friends and colleagues or use this knowledge to start a conversation. Let’s all do our part to #BeCyberSmart this Cyber Security Awareness Month.
CONTACT US TODAY TO DISCUSS YOUR CYBER SECURITY NEEDS
To find out more about our Cyber Security Services, click here.
To discuss your options and find out how we might help your business, get in touch today.
Email enquiries@wytech.co.uk | Call on 01335 670 007 | Complete our contact form

